Article
citation information:
Korecki, Z., Smrž, V.,
Bořil, J., Bauer, M. Ensuring aerodrome development processes and using
sensory networks. Scientific Journal of
Silesian University of Technology. Series Transport. 2018, 101, 99-117. ISSN: 0209-3324. DOI: https://doi.org/10.20858/sjsutst.2018.101.10.
Zbyšek Korecki[1], Vladimír Smrž [2], Jan Bořil[3],
Miloslav Bauer[4]
ENSURING AERODROME
DEVELOPMENT PROCESSES AND USING SENSORY NETWORKS
Summary. Using new technology to track
service movement and logistics equipment, passengers or wild animals in the
airport area can significantly reduce runway incursion occurrence. Sensor
implementation networks will allow for foreign entity identification in a
timely manner and take measures to prevent unauthorized access to the track.
Modern technologies, which include sensor networks, multifunctional camera
systems and radio frequency identification access chips facilitate the creation
of complex safety nets at active points and on access roads. Due to their
mobility and possible changes in range and direction, sensory networks are an
effective method for achieving the desired level of security. Combining
elements of modern technology creates space for automated airport security.
Security risk portfolios are now defined for 10 different operating domains and
give advice to the decision-making process, which the European Plan for
Aviation Safety (EPAS) has supported. The aim of the article is to analyse
safety in commercial air transport for the period 2006-2015 in comparison with
2016 and propose a method that would reduce the number of incidents through
sensor networks and using texture analysis.
Keywords: runway incursion; unauthorized entries;
hotspots; sensory systems
1. INTRODUCTION
The
primary aim of all actors involved in aviation is to keep all threats and risks
at an acceptable level, which is managed by two processes called safety and
security. The aim of safety is protecting people and property, including
environmental issues, against all possible system failures. The aim of security
is protecting people and property against acts of unlawful interference caused
by humans (i.e., terrorism or unadjusted passengers).
Measurement
of the level of aviation safety is achieved by introducing safety indicators.
By collecting, regularly evaluating and implementing knowledge gained through
security data analysis, it is possible to find events occurring under normal
operating conditions, as well as micro events that may represent the initiation
impulse of subsequent events defined in the ADREP/RIT Taxonomy of the
International Civil Aviation Organization (ICAO)[5] and the European Aviation Safety
Agency (EASA)[6].
Assuming
that near misses are the trigger mechanisms for events, we can find three base
layers of indicators based on the analysis of events measured by evaluating
state operational safety plans.
•
The
first layer presents accident statistics.
•
Reactive
indicators of the second layer give a more detailed view of the so-called
significant seven safety issues.
•
Proactive
third-layer indicators expand, in detail, the types of events in the second
layer to increase the data-generated quality of the event investigation.
2. Reactive indicators
definition
Reactive
indicators that represent the first layer include events of each type depending
on the severity and consequences of the event. The first layer consists of
accidents, incidents and deaths as described in ICAO Annex 13, ICAO Annex 19
and Regulation (EU) No 996/2010[7]. The first layer presents accident
statistics. As the data obtained from the first layer have no telling value,
second-layer indicators, which are predictive indicators, were added.
Reactive
indicators in the second layer give a more detailed view of the events of
so-called significant seven safety issues and are divided into seven types as
follows:
• Mid-air
collisions and near misses (MAC)
• Controlled flight
into terrain (CFIT)
• Runway incursion
(RI)
• Runway excursion
(RE)
• Loss of control
in flight (LOC-I)
• Ground collisions
(GCOL)
• ANS system
malfunction
Reactive
indicators, in view of their detail, allow us to explore interaction with each
other to the incidence reduction events between the different types of events
and the implemented measures.
Proactive
third-layer Indicators extend the second-layer event types in detail to
increase the event data quality.
In
event investigations, two variants of events can occur when factors of the
third layer could have been or were not identified at the peak event
occurrence.
The
research definition comes out from Regulation (EU) No 376/2014, which divides
events into four basic groups:
• Events related to
aircraft operation;
• Events relating
to technical conditions, maintenance and repair of an aircraft;
• Events relating
to air navigation services and equipment;
• Events related to
airports and ground services.
The
analysis based on compulsory and voluntary reports (IOSR) and reports produced
at national level (ECCAIRS) allowed us to find the most recurring collision
events between airplanes and other objects involve collisions of planes with
objects on the ground (vehicles, handling equipment and other objects). The
collision possibility is dependent on the level of an airport’s operating
environment controls, low-level knowledge of operating rules by airport personnel,
or the poor technical state of technical handling equipment.
An
important indicator concerns unauthorized track entry, where a runway is used
by another airplane or there is unauthorized access to the runway. The use of a
runway by another plane relates to low levels of crew/ANS communication,
technical problems with airport equipment, lighting and signage, or unclear map
data. Unauthorized entry of persons and wild animals relates to the low-level
physical security of the aerodrome area or a low level of ground clearance.
Another
important area is the failure to give or restrict air traffic management (ATM)
services provision.
This
indicator tracks events that have failed one of the systems providing
communication, navigation, tracking and data processing. The indicator is
physical and analyses the fault level of the ATM service provider.
The
International Civil Aviation Organization (ICAO) defines unauthorized access to
the runway as any occurrence at the aerodrome involving the unauthorized presence
of an aircraft, vehicle or person in a protected area of a landing and take-off
(runway) surface.
Unauthorized
entries on the runway are classified by incident severity from A to E (Table
1). The most important classifications for runway incursion prevention and
alerting systems (RIPAS) are Classifications A and B, where time is critical.
Classifications C and D should be detected by RIPAS, but do not need immediate
intervention.
Table
1
Classification of
track entry[8],[9]
|
Classification of severity |
Description |
|
A |
Serious incident to prevent collision. |
|
B |
An incident where there is a reduction in distance
and there is much potential for collision, which can lead to a time-critical
corrective/evasive response. |
|
C |
Incident characterized by sufficient time and/or
distance to avoid collision. |
|
D |
Incident that meets the runway intrusion definition,
such as the incorrect presence of a single vehicle, person or aircraft in a
protected area on the landing and take-off surface, but without immediate
safety implications. |
|
E |
Insufficient information or unconvincing or contradictory evidence hinders
the severity assessment. |
Air
carriers and large airports are usually equipped with technology for prevention
of intrusion onto the runway. The technical and financial constraints of
smaller airports are limiting the use of technology to prevent unauthorized
access to the runway.
Access
to the runway occurs in so-called “hotspots”, i.e., sites that the
ICAO defines as “areas to move to an airport with a history or potential
risk of an entry (on an airfield where pilots/drivers need increased.”
ICAO instructions for preventing runway collisions need to define the distance
to the runway, with permission usually transmitted via RTF or others form of
signals.
Detection
systems for unauthorized entry on the runway need to detect situations within 2
to 6 s. Earlier detection would make it possible to alert a ground vehicle to a
runway that has a lower speed and can better respond to the situation at an
early stage of the incident
The
European Organization for the Safety of Air Navigation (Eurocontrol) has stated
that the safety culture of incident reporting is not sufficient. In 2005, the
number of reported events amounted to 600 runway raids, with an upward trend of
almost 1,000 in 2008[10],[11]. According to the US Federal
Aviation Administration, the number of A and B disruptions since 2003 has been
decreasing, along with mileage between 2009 and 2010, when a program was
introduced to protect against unauthorized entry onto the runway.
The
ICAO and Eurocontrol have found that OEs and PDs form the main part of
unauthorized inputs on Type A and B runways. However, due to the high level of
dangers resulting from a change in safety levels, the technology to prevent
unauthorized inputs on the runway should preferably address VPDs and OEs and
handling activities.
2.1. Issues of so-called “hotspots”
Unauthorized
entry onto runways is mostly recorded at airport hotspots, which represent the
crossing of airport traffic corridors. Hotspots, as defined by
the ICAO, are “areas to move to an airport with a prediction or
potential risk of unauthorized entry to the runway requires attention of
pilots/drivers”. Ground collisions may occur during push-back and taxi
interference or foreign object debris in the manoeuvring area and apron[12].
Many
studies have shown that the frequency of unauthorized entry is related to the
number of runway crossings and airport layout characteristics. The ICAO
classifies unauthorized entries on the runway according to the following types
of causes: pilot deviation (PD), operational error/deviation (OE) and
vehicle/pedestrian deviation (VPD). Vehicle/pedestrian movement deviations
include pedestrians, vehicles or other objects that interfere with operations
and movements of aircraft, not approved by air traffic controllers. Under VPDs,
unauthorized access to runway service and logistics technology or passengers
may occur. Presence on the runway could be the cause of a collision between the
entities described on the runway or traffic fluency.
2.2. Track entry statistics
The
databases of the ICAO, the EASA and Eurocontrol have shown that the tendency of
unauthorized entries onto runways has been increasing in EASA countries due to
the increasing number of flight hours. According to annual reports, both the
number of passengers and the tonnage of transported cargo has increased. The
EASA is the EU agency responsible for the interpretation and enforcement of
member states’ rules and is superior to the national aviation authorities.
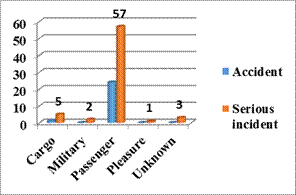
Fig. 1. Commercial air transport accidents and serious
accidents in operation[13]
2.3. Commercial air transport aircraft
EASA
AOC member states have a lower death rate per million flights than the rest of
the world. In 2006, the death rate was much below 0.5. Most accidents and
serious incidents still occur during the en route phase[14],
followed by take-off, approach and landing. Comparing the 10-year average of
different flight phases with real figures for 2015 shows an overall reduction
in accident rates for all phases of the flight. The same accident-specific
comparison shows an increase in incidents in the en route and take-off phases.
The types of accidents in these two phases are related to turbulence and
technical problems during take-off[15].
Key statistics of EASA AOC member
countries include data on accidents and serious incidents. It could be said
that the only fatal accident in the plane of a member state in 2015 was the
Germanwings accident. In 2015, a total of 24 fatalities was
recorded, exceeding the 10-year average, which accounted for 21.8 fatal
accidents. At the same time, serious incidents dropped by 24%, with 58 serious
incidents in 2015, while the 10-year average was 75.8. In 2015, there were 150
fatalities, meaning the 10-year average was exceeded. At the same time, in
2015, there was a slight increase in severe injuries, when there were 11
injuries, while the decade average was 9.2 injuries.
Vehicle/pedestrian deviations, which
could be defined in terms of the cargo/passenger ratio, were the main cause of
accidents or major accidents in 2015.
Table
2
Number of
accidents and serious incidents
on average during the flight phase: 2005-2014 vs. 2015
|
|
|
|
|
|
|
Standing |
Acc. avg. 2005-2014 |
4 |
Serious acc. avg. 2005-2014 |
3 |
|
Acc. 2015 |
3 |
Serious acc. 2015 |
2 |
|
|
Taxi |
Acc. avg. 2005-2014 |
4 |
Serious acc. avg. 2005-2014 |
3 |
|
Acc. 2015 |
7 |
Serious acc. 2015 |
5 |
|
|
Take-off |
Acc. avg. 2005-2014 |
2 |
Serious acc. avg. 2005 - 2014 |
6 |
|
Acc. 2015 |
17 |
Serious acc. 2015 |
11 |
|
|
En route |
Acc. avg. 2005-2014 |
3 |
Serious acc. avg. 2005 - 2014 |
7 |
|
Acc. 2015 |
30 |
Serious acc. 2015 |
23 |
|
|
Approach |
Acc. avg. 2005-2014 |
2 |
Serious acc. avg. 2005 - 2014 |
1 |
|
Acc. 2015 |
15 |
Serious acc. 2015 |
11 |
|
|
Landing |
Acc. avg. 2005-2014 |
7 |
Serious acc. avg. 2005 - 2014 |
5 |
|
Acc. 2015 |
9 |
Serious acc. 2015 |
3 |
2.4. Ground collisions and ground
handling
Hazardous areas concern
plane collisions with other planes, obstacles or vehicles. It is
necessary to take into account that a plane moves on the ground by its own
propulsion or by being towed. The risk area also includes all activities
related to ground handling (aircraft loading, refuelling etc.). It
could be said that 27% of fatal accidents will be caused by land
collisions and other related ground events in the decade to come. Given that
this is a growing trend, it is important to take action after a thorough
analysis to improve the current situation.
An analysis of vehicle/pedestrian
deviations (on runways) shows that the causes of unauthorized entry onto the
runway are roughly the same as if a ground vehicle driver entered the runway
area without authorization from the ATL department (usually ground or tower)
and in cases where the driver of the landing gear does not see a sufficient
distance in the holding area of the relevant runway. An overview of the factors
contributing to unauthorized access to the runway is given in Figure 2.
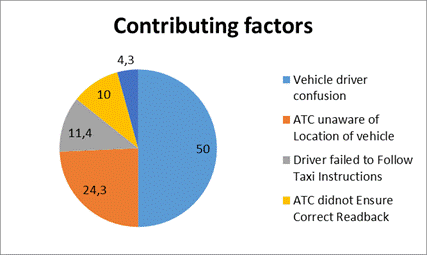
Fig. 2. Factors
contributing to unauthorized access to the runway by land-based drivers or by
persons moving over the airport’s operating areas
Another area under consideration is
the possibility to prevent or cut instances of unauthorized entry onto the
runway area, as summarized in Figure 4 below.
The International Air Transport
Association (IATA) has defined ground handling as follows: “It covers the
complex series of processes required to separate the plane from its load
(passengers, baggage, cargo and mail) on arrival and combine it with its load
before departure.”
Finding a solution to cut aircraft
collisions on a track with land-based vehicles or persons could be based
on the responsibility definition for finding measures. Responsibility
for the safety of ground operations lies with the member state.
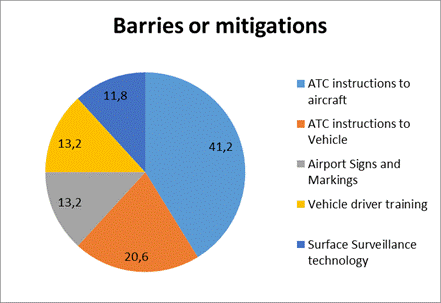
Fig. 3. Possibilities to prevent or
cut instances of unauthorized entry onto the runway
3. Theory
of intrusion prevention systems
Existing risk identification in
ground handling operations is based on detailed mapping of subjects, the action
interface and the daily routine of activities, including a time map. The data
obtained could be further used for later analysis.
An analysis of available literature
is the result of Table 3, which provides a comprehensive overview of the
subjects involved in the ground clearance process.
Table
3
Phase and
ground movement activity
|
Phase |
Define activity content |
|
Taxiing after landing |
The phase starts
when you leave the runway after the landing and ends when you arrive at the
check-in area. The plane is powered by its own drive. |
|
Standing on apron |
The
phase begins when the plane arrives at the ramp and stops at the assigned
stand. The plane is in motion at this stage. |
|
Exploding the plane from the stand |
The airplane is
pushed from the stall to a defined area (and direction) by a tractor to the
ramp, from where it moves on its own. |
|
Taxiing to start |
The phase begins
when the plane begins to move by its own drive from the ground and ends at
the arrival point of the runway. |
The total number of ground handling
incidents in the analysed period reached 2,841 for 14 million flights. It
could be said that this equates to one incident per 5,000 flights.
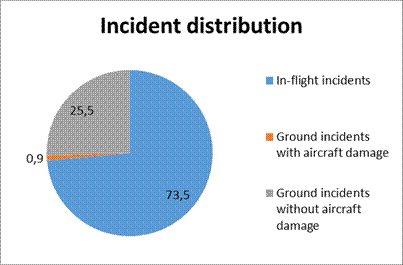
Fig. 4. Breakdown of incidents
26.4% of incidents are associated
with ground events, with 0.9% resulting in damage to the plane. Figure 5 shows that
most (84%) ground accidents occur when the plane is in motion.
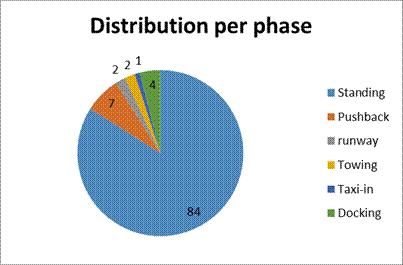
Fig. 5. Incident breakdown by phases
Most incidents occur at the standing
stage; the authors only analysed those who enter this phase. The bodies that
cause ground incidents are described in Figure 6, which also expresses the
number of incidents caused by ground entities.
Figure 6 provides information on
which entities are most involved in ground incidents.
The most significant actors involved in ground incidents in relation to the
total number of incidents are listed in Table 4.
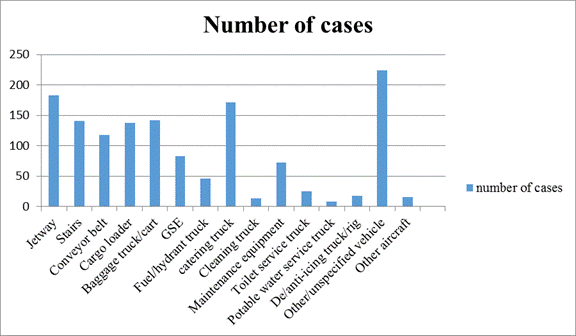
Fig. 6.
Breakdown of incidents by subjects
Table 4
The ranking of subjects by
land-based incidence
|
Subject |
Incidence rate (%) |
|
Other/unspecified vehicle |
16.3 |
|
Jetway |
13.1 |
|
Catering truck |
11.8 |
|
Ground service equipment |
10.1 |
|
Stairs |
8.9 |
4. Sensory systems
Sensor systems allow for capturing phenomena
in many ways and the identification processes based at the airport for ground
operations. Modern technology allows us to track multiple identified phenomena
at the same time. The system suitability for the selected airport is
determined by the security need. At present, SMR and ASDE surveillance radars
are used at the airport, but they could be exchanged with a camera system.
The aerodrome subjects’ connectivity
could be achieved through technological means by the implementation of
digitizing systems. Key elements include a tele-information network, a sensor
network, a satellite telecommunication network, digital communication systems
and radio frequencies, unmanned vehicles and nanotechnology[16].
Combining different types of video capture
with a camera system, which has enough motion detection accuracy, could be an
alternative to radar.
Combining cameras (classic security and
infrared) will increase the accuracy of motion detection with the place of
determination for the object in the order of metres, especially for larger
objects. The surveillance camera system at small airports could be used
primarily to check traffic in operating areas.
4.1. MicroTrack - detection of perimeter disruption
A system of ground coaxial cables allows for
the detection of perimeter disruption through an electromagnetic field.
Deviation in electromagnetic field values prompts the launch of airport
security activities.
The system creates fields with specified
characteristics, and the change in characteristics gives information about a
non-standard object in the electromagnetic field. Diverse levels of
electromagnetic field disturbance make it possible to find the size of the
object and the resulting potential hazard. The system uses two basic
configurations:
1.
Measurement
of electromagnetic field distribution change
2.
Amplitude
and frequency change
The perimeter secured by the pairs of cable
systems has a 150-200-m zone dimension and generates a magnetic field that is
about 3 m wide and 1 m high over its entire length.
The size of the magnetic field depends on the
factors as follows:
1.
Measurement
of electromagnetic field distribution change
2.
Subsoil
3.
Material
4.
Other
surrounding lines
5.
Spacing
from surrounding objects and metallic structures
Measurement deviation is several metres long
and the security system could be complemented by closed-circuit television
(CCTV). Each scanned zone could be set separately, due to different
environments.
4.2. Analysis of crowd movement in real time
The system is the superstructure of motion
video abnormal motion detection. Rather than an individual object, the movement
of a whole group of people is analysed using motion vectors in the “mask
of space”. The mask of space is defined by the characteristic features of
the environment, which may be typical directions of movement in the given areas
of the mask.
Identifying environmental characters will
allow us to define so-called hot and cold places, characterized by different
levels of occupancy of group movements. Defining the mask will allow the
analysis of group movement. The system based on the normal direction of
movement and behaviour in the crowd is a common phenomenon of much concern. The
algorithm of normal motion and behaviour can later find an abnormal phenomenon,
which is a basic condition for further activities[17].
Fig.
7. MicroTrack detection[18]
Passenger movement in airport areas is a
complex architecture, which is based on a specific national behavioural
culture, the architecture of the inner and outer infrastructure of the terminal
and the airport, and the conditions for the visual supervision realization.
The main processes are:
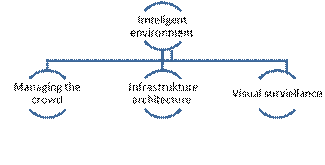
Fig.
8. Management of crowd movement control in the terminal
An analysis of crowd movement at the
time windows will serve to propose a change in the environment with respect to
the disconnection point’s elimination of and the narrow throat to
increase the flow of passengers’ continuity.
4.3. Tracking crowd movement in crowded space
Finding connections to passengers’
movement in the terminal’s internal spaces is an important factor
enabling the same person identified in a time sequence within defined spaces.
The architecture of the airport clearly determines the trajectory of
people’s movement, and identifies the main flows of the crowd and the
deviations in personal behaviour. This process serves to find abnormal
behaviour. It is clear that theories of chaos can apply here, where the
diverging crowd could be deviated from the supposed movement of the crowd. The
task of airport security structures is to find serious violations of motion
algorithms, and to find risk behaviour based on general knowledge of the
interior. Complications with risk identification increase with traffic density.
A proper behaviour algorithm set-up also
requires an appropriate taxonomy of approaches. Identifying suspicious
behaviour in the crowd requires analysing the number of people, while monitoring
individual people or groups. The goal of the activities is to find participants
in the crowd, regardless of their place and timing.
Track-to-person activities require the exact
location of each person in the internal or external areas of the airport while
identifying the time sequences of movement and the static positions of persons
or groups. It is possible to accept the idea that some approaches, which are
used to count people in objects, could be applied to define people-tracking
algorithms. Appropriate motion algorithm settings could be used to count people
in the crowd as well as track them.
Processes associated with counting people in
the crowd also allow for tracking of traces of movement in the target mask. A
person’s movement in a “bottleneck” is likely the reflect the
patterns of behaviour of people in the crowd. Empirical experience shows that
people group themselves into “group songs”, which move to each
track at constant speeds. By analysing group tracks, the inclusive behaviour of
people or groups could therefore be identified more quickly if crowd density is
at an acceptable level[19],[20].
Structured scenarios for a person’s
movement in a conceived crowd structure require video
sequences divided into cells, which move in a defined space with different
architectural solutions that must move everyone in a crowd continuously while
completely avoiding obstacles and barriers[21]. The
automatic movement of people in a crowd later allows us to find different
behaviours of persons or groups.
Group behaviour research, which has been
carried out for many years, has simulated the behaviour of the crowd in
different modelled situations. The aim here has been to check the general view
of group behaviour, with the results used to improve the level of crowd analysis.
Created algorithms for computer vision, which
are used to analyse the crowd, could be applied to improve the use of life
information and to aid in the realistic display of crowd synthesis algorithms[22],[23].
The spatial distribution of the crowd in real space could be used to create
a crowd behaviour simulator[24],[25],[26],
while the observed main directions of crowd movement could be used for
simulation[27],[28],[29].
5. Surveillance based on multi-picture
capturing
The airport security overview uses
surveillance radars known as surface movement radar and aerodrome surface
detection equipment.
5.1. Ground surveillance radar
Primary surveillance radars are the most
widely used means of detecting motion at large airports. They allow air traffic
control and airport traffic to cut collisions and trajectory disturbances.
Survey radars also cover areas between traffic areas to give a complete
overview of the airport’s perimeter situation.
The sensitivity requirement could be
interpreted as follows:
1.
Detection
of all objects in the aerodrome, where the least reflective area of the target
is 1-3 m2.
- Scanning
space within the range of 0-100 m.
- The
refresh rate is at least 60 frames/min.
4.
Radar
ability to detect all targets with a speed of 0-450 km/h.
5.
Reliable
detection in all-weather conditions up to 100 mm/h.
6. Differentiating two
nearby objects.
7. Deviation of target
location detection in metres.
- Responding
to false reflections on large reflective surfaces.
5.2. Multimedial sensor
system in foreign object damage on runway detection
In the current state, the occurrence of foreign object damage (FOD) on the
runway is continually controlled by ground handling at the airport, with
deteriorating weather or night-time conditions significantly reducing control
efficiency. New technologies make use of the ability to automatically detect
FOD on the desktop and invoke subsequent activities to ensure security.
System sensors positioned along the track can
continuously capture the track surface and detect objects under all climatic
conditions. The sensors are equipped with an infrared camera, as well as an
optical two- and three-dimensional camera, and connected to the radar
sensors.
Linking with the optical system allows us to
find the object on the desktop. Sharing information will allow the transfer of
the operator who performs the removal of the object from the track. The person
sensor has a 700-m radius. False signals caused by animals, birds or small
objects moved by wind are eliminated by the need for an object to stay
static for a defined minimum duration[30].
5.3. Detection of FOD
and PID[31] microwave radar
Tarsier systems and SMART have been developed
to detect FOD based on microwave radar[32].
In order to cover an adequate part of the perimeter, the radar placed at a
minimum height of 10 m above ground level, with a specific placement,
also needs to allow FOD, PID and tracking movements at the airport.
Microwave radars run on wavelength ranges
between 94.5 and 95 GHz and a beam width between 0.28 and 0.3° allow for
the detection of small objects according to their type, up to a distance of 1-2
km with an accuracy of about 2.5 m[33].
The systems are supplemented with optical
sensors for precise focus and object evaluation. The disadvantage is that they
only detect only small metal and dielectric objects. Technological development
is still beyond the limits of use of these systems. Technological advances in
systems are increasing accuracy in terms of focus and resilience, which
contributes to improved security.
6. Recommendation
The authors recommend the use of the texture
analysis method, which represents complex visual patterns of subjects or masks
of spaces with characteristic brightness, colour and size. An important fact is
that local spaces involve different uniformities of space, densities of the
crowd, regularities of movement, linearities of behaviour and frequencies of
movement[34].
Four basic problems of texture analysis were defined[35].
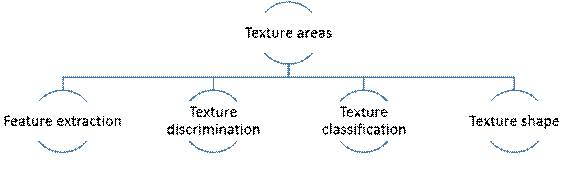
Fig. 9. Texture problematic areas
Feature extraction is the first stage where
the security manager will use structural, statistical, modelling and
transformation methods.
Structural approaches for resolving the
texture represent a suitably defined microtexture with a clearly formed
macrotexture spatial arrangement hierarchy[36],[37],[38].
To describe the texture, it is necessary to
define the basic rules of the warp movement of the crowd and the rules of
placement in the space. The choice of base fibres is based on the
characteristics of the set and the crowd moving opportunity along the selected
base fibres. The approach assumes that the occupants will occupy certain places
or the surrounding area, allowing for a sufficient description of reality used
for synthesis and analysis.
Abstraction
of the texture description could be affected by the insufficient definition of
texture threads due to the variability of microprocesses and macrostructures.
The problem may also be concerned with the lack of clarity between
microtextures and macrotextures. The use of mathematical morphology is a proper
tool for structural analysis[39],[40].
We can use
the autoregressive model expressed by the formula:
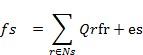
where fs is the in
situ image intensity, which indicates an independent variable and the equally
distributed noise, Ns is the adjacent element s, and θ is the model
parameter vector.
Another
useful model is Markov’s random field, which represents the chance of the
process of interacting with all local elements. The model is based on the
assumption that cell similarity is quite likely in a given state among adjacent
cells[41],[42].
As a result, direct interaction occurs only between the immediate neighbours.
However, Markov’s random field may change as a result of promotion within
a globalized world[43].
![]()
Another
useful model for crowd movement is the fractal model, which represents fractal observations
and shows a strong correlation with human judgement, based on crowd
movement intensity, and predictable narrowing. The correct distribution of
the crowd movement fibres, including the linear motion logarithm spectrum, is
suitable for texture creation and thus suitable for modelling[44].
7. Conclusion
The
use of sensor networks is based on the correct identification of ground
handling and movement processes for persons, wild animals and logistics
vehicles in the internal and external aerodrome areas. By using sensor systems
combined with CCTV, the level of safety and incident reductions in unauthorized
entrances on the runway will increase, as well as reducing the number of
airport staff needed. Based on the assumption that the human factor is the
greatest risk to security controls, it could be assumed that the massive use of
technology will cut error rates while allowing staff to prepare themselves to
cut incidents through direct intervention.
Ground-based
air traffic safety services are activities associated with runways, handling
ground operations and the maintenance of working areas. A solution to
increasing safety is the use of sensor network capabilities and optical camera
systems to analyse abnormalities. It is necessary for future surveillance systems
to allow the airport’s security components to determine the
movement-related abnormality with the security vehicles’ movement and the
person’s movement in defined masks, and enable the readiness of these
components to limit the abnormal effects.
The
combination of modern surveillance technology for crowd and service vehicles
and MicroTrack, in order to guard the perimeter, will allow us to control
defined zones and track people in all areas of the airport. The use of sensors
in camera systems will enable a high level of air traffic safety.
Different airport characteristics will need different approaches to the sensor
network’s configuration. The determinants of networking are influenced by
the level of the building infrastructure, the transport network, people
movement prediction and the crowd in the defined motion masks.
References
1.
Andrade
E.L., S. Blunsden, R.B. Fisher. “Modelling Crowd Scenes for Event
Detection”. Proceedings of the
International Conference on Pattern Recognition: 175-178. Washington, DC.
2.
Andrade
E.L., R.B. Fisher. 2005. “Simulation of Crowd Problems for Computer
Vision”. Proceedings of the First
International Workshop on Crowd Simulation: 71-80.
3.
Bentyn
Z. 2017. “Logistic performance development of the countries on the
northern corridor of the new silk road”. European Transport \ Trasporti Europei. Issue 63. Paper no 4:
1-15.
4.
Blake
A., A. Zisserman. 1987. Visual
Reconstruction. The MIT Press.
5.
Brodatz
P. 1966. Textures - A Photographic Album
for Artists and Designers. Mineola, NY: Dover.
6.
Campbell
N.D.F., K. Subr, J. Kautz. N.d. “Fully-connected CRFs with Non-parametric
Pairwise Potentials”. Available at:
http://homepages.inf.ed.ac.uk/ksubr/Files/Papers/PrwPotPaper.pdf.
7.
Chen
Y., E. Dougherty. 1994. “Grey-scale Morphological Granulometric Texture
Classification”. Optical
Engineering 33(8): 2713-2722.
8.
Courty
N., T. Corpetti. “Crowd Motion Capture”. Computer Animation and Virtual Worlds 18(4-5): 361-370.
9.
D’amato
A.A., S. Kgoed, G. Swanepoel, J. Walters, A. Drotskie, P.J. Kilbourn. “Convergence
of logistics planning and execution in outsourcing”. Journal of Transport and Supply Chain Management 9(1)(a159): 1-9.
DOI: https://doi.org/10.4102/jtscm.v9i1.159.
10. Dukiewicz T. 2016. “Systém ISTAR jako
determinanta vojenského informačního
prostředí”. International
Military Technical Conference Tactics 2016. Brno. [In Czech: “ISTAR
as a Determinant of the Military Information Environment”.] ISBN
978-80-7231-398-3.
11. EASA. Reduced
Interface Taxonomy.
12. EASA. Annual
Safety Review 2016. Available at:
https://www.easa.europa.eu/sites/default/files/dfu/209735_EASA_ASR_MAIN_REPORT.pd.
13. Eurocontrol. 2009. Annual
Safety Report 2009. Eurocontrol.
14. Eurocontrol. 2010. Annual
Safety Report 2010. Eurocontrol.
15. Haell C.H., J.T. Lundgren, S. Voss. 2015.
„Evaluating the performance of a dial-a-ride service using
simulation”. Public Transport
7(2): 139-157.
16. Haralick R. 1979. “Statistical and Structural
Approaches to Texture”. Proceedings of the IEEE 67(5): 786-804.
17. Heinrich H.W. 1931. Industrial Accident Prevention: A Scientific Approach. New York,
NY: McGraw-Hill. Quoted in E. Hollnagel. 2009. Safer Complex Industrial Environments: A Human Factors Approach.
Boca Raton, FL: CRC Press. ISBN 1-4200-9248-0.
18. Hotař V. 2009. “Definice
fraktálů”. [In Czech: “Definition of fractals”.]
In Metodika popisu
průmyslových dat pomocí fraktální geometrie.
[In Czech: Methodology for the
Description of Industrial Data Using Fractal Geometry.] Liberec:
Technická univerzita. Available at:
http://www.ksr.tul.cz/fraktaly/definice.html.
19. ICAO. 2000. ADREP
2000 Taxonomy.
20. ICAO. 2007. Doc
9870 - AN/463, Manual on the Prevention of Runway Incursions. International
Civil Aviation Organization.
21. ICAO Meeting GRSS. Available at:
https://www.icao.int/Meetings/GRSS-2/Documents/Panel%202/P2.2_FAA.pdf.
22. ICAO. Official Definition, Annex 6/III Operation of
Aircraft - International Operations - Helicopters 2010. Available at:
https://ext.eurocontrol.int/lexicon/index.php/En-route_phase.
23. INTREPIDTM MicroWave 330, Digital Microwave
Link. Southwest Microwave. Available at:
http://www.southwestmicrowave.com/pdfs/MicroWave-330-Data-Sheet-EN.pdf.
24. Jacques, Jr., J.C.S., A. Braun, J. Soldera, S.R.
Musse, C.R. Jung. 2007. “Understanding People Motion in Video Sequences
Using Voronoi Diagrams”. Pattern
Analysis and Applications 10(4): 321-332.
25. Levine M. 1985. Vision
in Man and Machine. New York, NY: McGraw-Hill.
26. Murphy K.P.
N.d. “Undirected Graphical Models (Markov Random Fields)”. Machine Learning: A Probabilistic
Perspective. Available at:
https://www.cs.ubc.ca/~murphyk/MLbook/pml-print3-ch19.pdf.
27. Musse S.R., C.R. Jung, J.C.S. Jacques, Jr., A. Braun.
2007. “Using Computer Vision to Simulate the Motion of Virtual
Agents”. Computer Animation and
Virtual Worlds 18(2): 83-93.
28. Musse S.R., M. Paravisi, R. Rodrigues, J.C.S. Jacques,
Jnr., C.R. Jung. 2007. “Using Synthetic Ground Truth Data to Evaluate
Computer Vision Techniques”. Proceedings
of the IEEE International Workshop on Performance Evaluation of Tracking and
Surveillance: 25-32.
29. Paravisi M., A. Werhli, J.C.S. Jacques, Jr., R.
Rodrigues, A. Bicho, C. Jung, S.R. Musse. 2008. “Continuum Crowds with
Local Control”. Proceedings of
Computer Graphics International (CGI’08): 108-115. Istanbul, Turkey.
June 2008.
30. Pham T.A. 2010. Optimization
of Texture Feature Extraction Algorithm. Available at:
http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.827.8904&rep=rep1&type=pdf
31. Pour A.T., S. Moridpour, A. Rajabifard, R. Tay. “Spatial
and temporal distribution of pedestrian crashes in Melbourne metropolitan area”.
Road & Transport Research 26(1):
6-22.
32. Rittsche J., P.H. Tu, N. Krahnstoeve. 2005.
“Simultaneous Estimation of Segmentation and Shape”. Proceedings of Computer Vision and Pattern
Recognition 2: 486-493. Washington, DC.
33. Serra J. 1982. Image
Analysis and Mathematical Morphology. Cambridge, MA: Academic Press.
34. Solera F., S. Calderara, R. Cucchiara. 2016.
“Socially Constrained Structural Learning for Groups Detection in
Crowd”. IEEE Transaction on Pattern
Analysis and Machine Intelligence 38 (5): 995-1008.
35. Stroeve S., P. Som, B. van Doorn, B. Bakker. 2015
“A Risk-based Framework for Assessment of Runway Incursion Events”.
11th USA/Europe Air Traffic Management
Research and Development Seminar (ATM2015). Available at:
http://www.atmseminar.org/seminarContent/seminar11/papers/366_Stroeve_0121150328-Final-Paper-4-23-15.pdf.
36. Taylor G., A. Chosak, P. Brewer. 2007. “OVVV:
Using Virtual Worlds to Design and Evaluate Surveillance Systems”. Proceedings of the IEEE Conference on
Computer Vision and Pattern Recognition: 1-8.
Received 18.07.2018; accepted in revised form 24.10.2018
![]()
Scientific
Journal of Silesian University of Technology. Series Transport is licensed
under a Creative Commons Attribution 4.0 International License